CaptchaJacking - An Approach to Bypassing the Captcha
Hi everyone.
Let me introduce myself – my name is Shubham, and I enjoy infosec. The PoC for CaptchaJacking Reddit is further down into the blog post.
Let’s face it.
Most captchas are outdated. Take the example below. How would one normally bypass a captcha system like this? Well, most would suggest creating an algorithm or program to bypass this captcha. Correct? Yes. You can definitely bypass captchas by using software to figure them out and punch them through. This is discussed here. But really, CaptchaJacking is a new way to bypass captchas, which really doesn’t require any complex algorithms but rather unsuspecting victims.
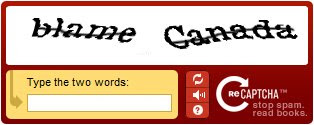
[1] Outdated recaptcha system – which doesn’t work
Now lets take a few things into account:
- The image within the captcha can usually be grabbed using a bit of logical thinking and/or regex
- These captcha images can be then saved or relayed anywhere you like.
- So… why can’t captchas be hijacked, and why can’t we use people signing up or validating captchas on our website to unsuspectingly create some yummy and fresh spam accounts for us?
There’s no reason why you can’t really.
What you need to captchajack successfully:
~100 x Socks5 proxies
100,000 x emails to spam [Spam Victims]
1 x Website which uses image based captchas [Victim Website]
Note: Socks proxies used for each request to the victim website
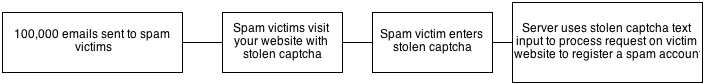
1. Create a web application which grabs the captcha from the victim website, and stores it locally.
2. In any form of your website, when wanting to validate users – show the captcha from the victim site
3. Send spam emails to 100,000 people (hoping that the email list you used is not a crappy one)
4. Every captcha someone enters into your website and submits, gets handled on the server side to send a request to the website you want to create spam accounts on, to actually create an account on our victim website – using our spam victims captcha string.
5. If the captcha went through and an account is successfully created, accept the spam victims input, else: grab a new captcha and show it to the victim.
Here is a little diagram for those which didn’t quite get what I said above:
Great. The concept sounds cool! Now let’s put CaptchaJacking to play. Proof of concept below.
Before I start firing away how I made it work, here are the limitations of my PoC *(most are easy to fix and are deliberately placed so spammers can’t just use my code as an out of the box option):
- My code has no proxy support as of yet
- It only grabs one captcha everytime the script is started up (deliberate but easily fixable)
- It’s a PoC which works on reddit.com only
My tools for the PoC:
- CherryPy Webserver (Lightweight, easy to use and python)
- Mechanize and Sessions Python Libraries (Mechanize for bot like browsing, Requests for general queries)
Note: In order for the proof of concept to work, you will need the libraries CherryPy, Mechanize and requests. All of these can be installed via “easy_install” or “pip”.
Here is a GIF of the process:
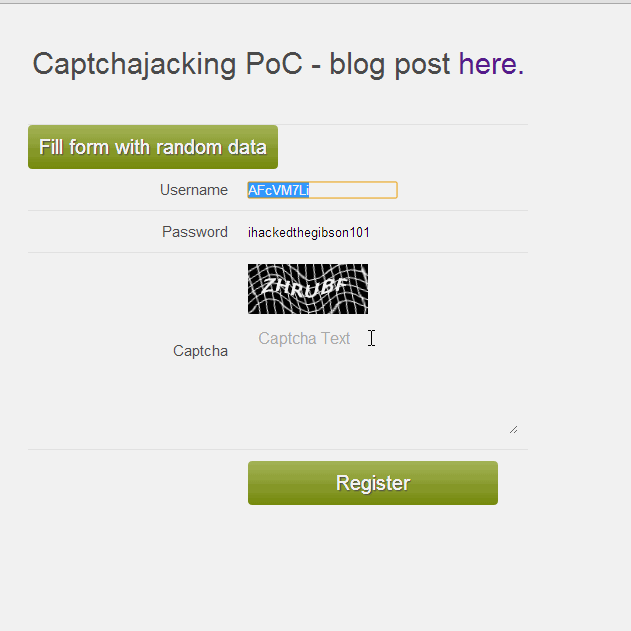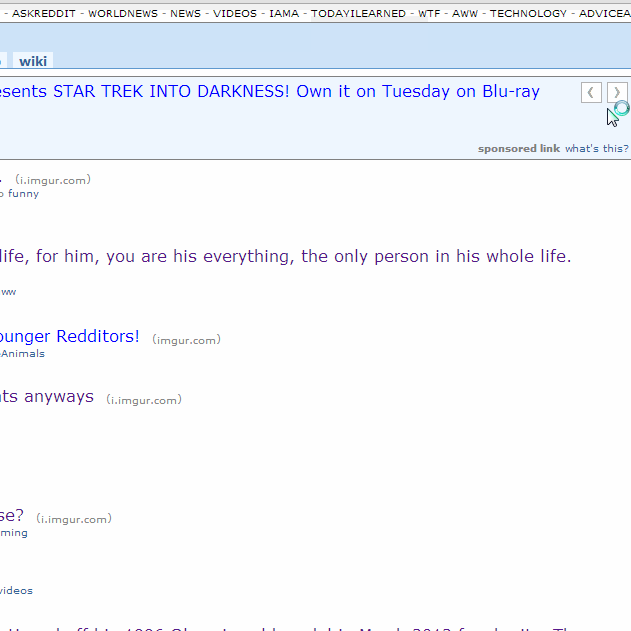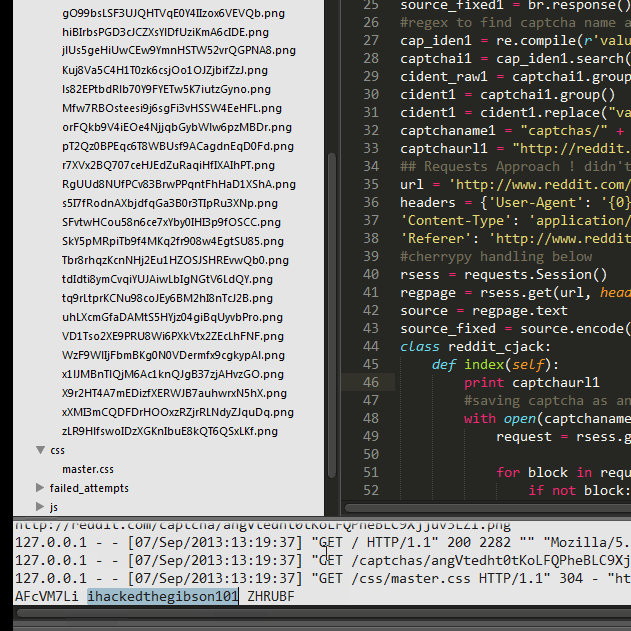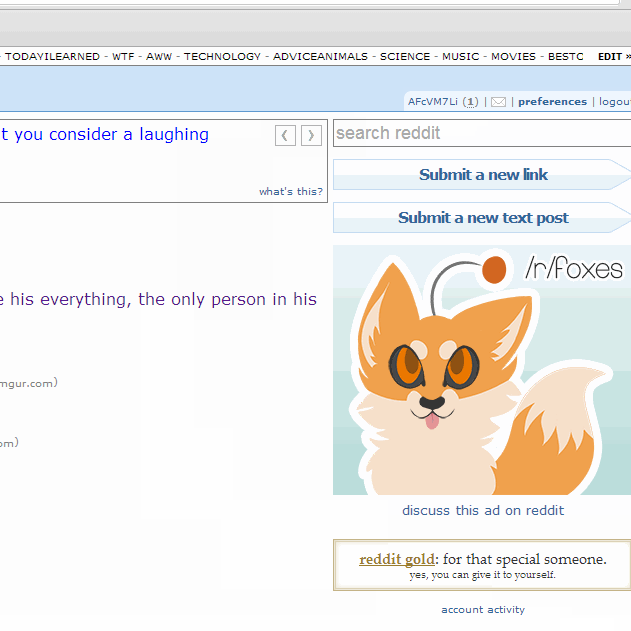
Here are the PoC files:
https://github.com/infosec-au/CaptchaJackingPoC
Thanks for reading!
