Abusing URL Shortners to discover sensitive resources or assets
As of late, a fair few companies and startups have been using dedicated URL shortner services to use for tracking and social media purposes. An example link from such URL shortners look like this invent.ge/1j1QxGo or invent.ge/DNATool. Note that both custom words and generated random letters+numbers can be used when shortening a URL.
While I was looking at some domains with @0xkitty for bug bounties, we found an interesting attack vector to extract internal or sensitive URLs from URL shortners.
The specific method describes how its possible to salvage a bunch of potentially sensitive/or confidential URLs via the Bit.ly SaaS used by a large number of corporations (and those who offer bounties).
X corporation uses the URL shortner domain http://xyz.com. We can check whether or not it's a Bitly URL shortner service by visiting http://xyz.com/debug.
This will return the following if the URL shortner is powered by Bitly:
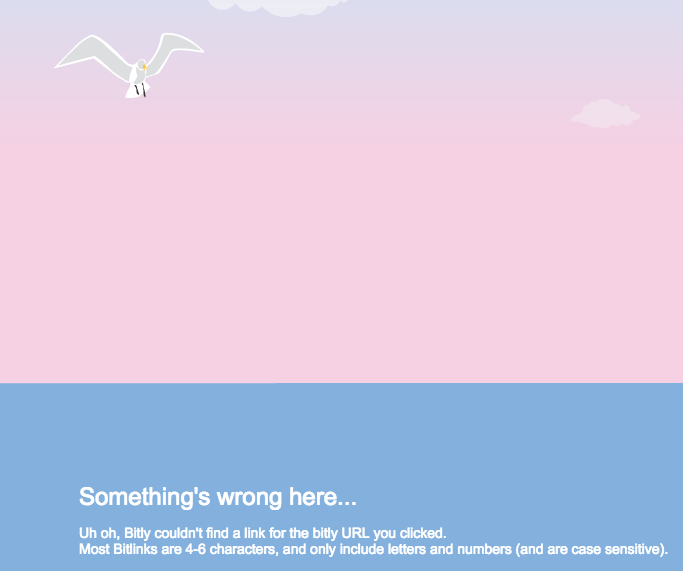
We can now run a directory/file bruteforce on this URL shortner service in order to find links that have been generated by staff at said company through the shortner.
For example, by using the dirs3arch tool we can brute this Bitly endpoint in order to find URLs that could potentially be sensitive.
I ran the following command for only 2-5 minutes.
Note: xyz.com is merely an example of a Bitly powered URL shortner, it's not an acutal Bitly shortner. It has been used to avoid listing any companies that actually do use Bitly's shortner.
root@vulnscanningyo:~/pentest/dirs3arch# python3 dirs3arch.py -u http://xyz.com/ -e php,html -t 5 -w db/dirbuster/directory-list-2.3-medium.txt -x 403 2>&1 | tee results1.txt
To then filter out all the valid results, we can use this simple python script:
with open("results1.txt","r") as fp:
for line in fp:
if "106B" not in line:
print line
Running the above script returned the following results:
[03:31:05] 302 - 189B - /10 -> http://xyz-long-url.com/10?geo=global&utm_medium=social_organic&utm_source=all&utm_campaign=xyz10
[03:31:06] 410 - 9KB - /login.php
[03:31:06] 302 - 124B - /events -> https://www.xyz-long-url.com/community/events
[03:31:11] 302 - 123B - /copyright -> http://www.xyz-long-url.com/help/article/263
[03:31:11] 302 - 165B - /subscribe -> https://www.xyz-long-url.com/your/account/email?ref=fp_ln_emails&action=edit_lists
[03:31:13] 302 - 183B - /library -> https://docs.google.com/a/xyz-long-url.com/forms/d/1q_U1_cxt6OMrDupANfcb4btNN_xxxxxxxxxxx/viewform
[03:31:16] 302 - 113B - /mobile -> http://www.xyz-long-url.com/mobile
[03:31:16] 302 - 123B - /policy -> http://www.xyz-long-url.com/help/article/483
[03:31:21] 302 - 116B - /post -> http://xyz-long-url.com/promos/xyz/
[03:31:22] 302 - 119B - /FAQ -> https://www.xyz-long-url.com/help/topics
[03:31:25] 302 - 113B - /local -> https://www.xyz-long-url.com/local
[03:31:28] 302 - 173B - /policies -> http://www.xyz-long-url.com/blog/en/2012/service-tips-for-sellers-creating-policies-that-work/
[03:31:28] 410 - 9KB - /wp-login.php
[03:31:29] 302 - 145B - /development -> https://jira.xyz-long-url-internal.com/confluence/display/AV/XYZ+Development
From this simple abuse method we've been able to expand our attack scope and gain some knowledge about XYZ corp's internal URLs. Some URLs that were found in the quick 3-5 min bruteforce also included Google Doc forms and potentially other hard to find/sensitive links.
Applying this same method over other URL shortners will also work, however they may rate limit you so you may need to use proxies in order to extract as much as possible, blindly.
I thought this was just another cool trick/way of expanding an attack scope so I felt like it was worthy of a blog post. If you like this post, say hi to @infosec_au and @0xkitty on twitter :)
