"wont fix" Persistent XSS on eBay member pages
Today I would like to disclose an XSS vulnerability present on members.ebay.com which the security engineering team at eBay.com do not classify as a security issue.
To test the PoC further down, you must have an eBay account.
This is the logic behind the vulnerability:
1. eBay allows for users to create their own “member” pages which can contain HTML
2. When HTML with JavaScript such as <script>alert(document.cookie)</script> is submitted they actively prevent it from being used on the member page.
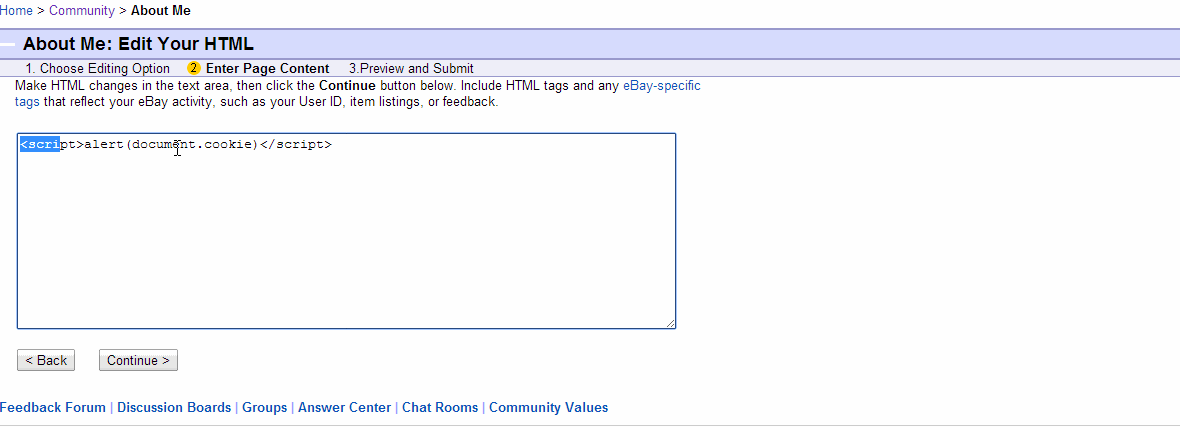
3. However, I thought, why not just obfuscate the JavaScript? Of course we can! A quick option for me was to use this obfuscator. It worked perfectly.
4. An obfuscated version of:
<script>alert(document.cookie)</script>
looks like this:
<script type="text/javascript">//<![CDATA[var _0x64f5=["\x63\x6F\x6F\x6B\x69\x65"];alert(document[_0x64f5[0]]);// ]]></script>
The GIF below demonstrates the successful submission of the JS code above:
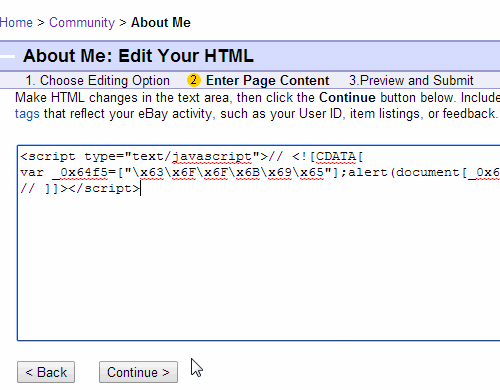
5. The javascript executes perfectly.
Now, whilst eBay session cookies are HttpOnly, there are still quite a few nasty things which can be done via such an XSS.
It may even be possible to spurt a JS worm and cause mayhem. I haven’t really experimented further – but eBay does not consider this a security issue – but rather to them, it’s a “function” which they allow for users to use. Below is my conversation with the eBay site security team (please click it so that you can zoom in and read the text):
Here are the emails from the eBay security team, stating that they are not willing to fix this issue:
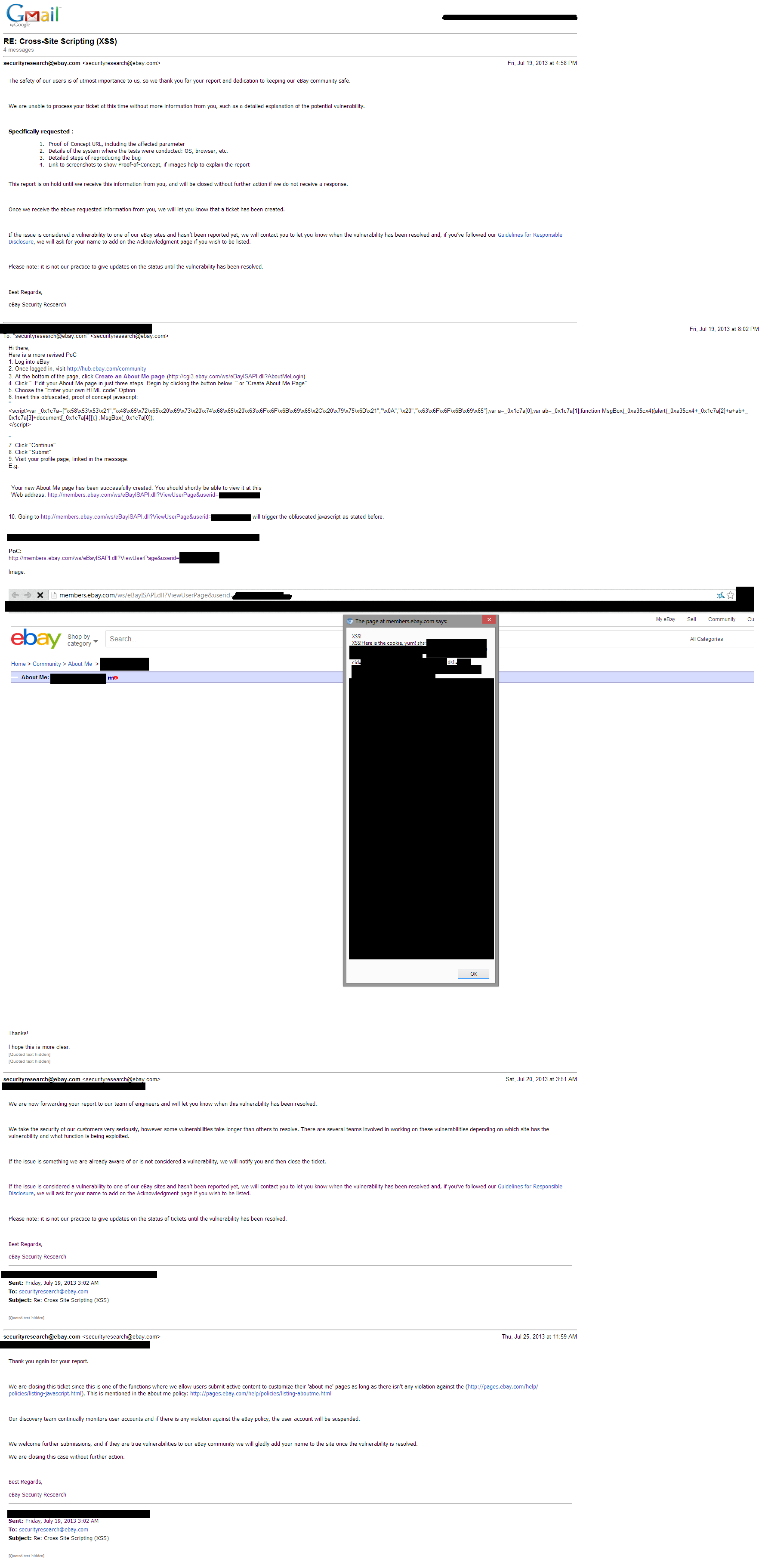
In short:
eBay tries to block such JS submissions through a filter – and that filter can by bypassed through JS obfuscation, allowing for almost everything above to be possible. This is why this is considered a security vulnerability in my perspective at least.
Additionally, they state that they remove accounts which violate the terms and conditions. I’m somewhat skeptical of that due to the large nature of eBay as well as the fact that they haven’t quite removed my account which has been sitting there with evil JS for around 2 months.
Nonetheless, it was fun finding this bug. Not that complex, but can prove to be scary. I hope eBay fixes it or applies a stricter criteria perhaps.
Thanks for reading, and thanks to the efforts of the eBay security team, regardless of this vulnerability – as I am sure they have dealt with many more serious vulnerabilities than this one.
Be sure to disable scripts when visiting members.ebay.com
Thanks for reading,
Shubham
